In the ocean of blockchain topics in the web space, we frequently encounter blockchain-idealists’ beautiful fundamentalistic mantras: popular ones are often associated with disintermediation (elimination of middlemen) and peer-to-peer system. In a way, these contemplate a paradigm of transaction without friction. It casts a radical notion: a blockchain-base distributed system can eliminate rent-seeking intermediaries and, as a result, deter, or even eliminate an abuse of the system by monopolist and oligarchs.
However, the reality of blockchain as of today is far from, is even contrary to, such radical notions. The gap between the popular fundamentalistic mantras and reality has caused confusions about blockchain.
Despite the gap, their beautiful mantras continue to echo and have strong influence in shaping our collective perception about and our collective behaviour toward blockchain.
Are those mantras really viable ideas? Are those blockchain idealists hypnotising us with deceptive mantras? Or, are we in the middle of a long journey to realise such a radical revolution in the way we organise transactions?
This series explores causes for the confusion from the following three perspectives.
In a way, the first blog narrowed the scope of our journey to one specific type of blockchain, “permission-less, public blockchain.”
Now, the second blog of this series continues the search for another potential suspect that accounts for the confusion. It questions the viability of the cornerstone of “permission-less, public blockchain,” consensus protocols.
However, the reality of blockchain as of today is far from, is even contrary to, such radical notions. The gap between the popular fundamentalistic mantras and reality has caused confusions about blockchain.
Despite the gap, their beautiful mantras continue to echo and have strong influence in shaping our collective perception about and our collective behaviour toward blockchain.
Are those mantras really viable ideas? Are those blockchain idealists hypnotising us with deceptive mantras? Or, are we in the middle of a long journey to realise such a radical revolution in the way we organise transactions?
This series explores causes for the confusion from the following three perspectives.
- Linguistic ambiguity in literature;
- Limitations in Consensus Protocols—Trilemma and Concentration Curse;
- Myth-conceptions—myth arising from misconceptions;
In a way, the first blog narrowed the scope of our journey to one specific type of blockchain, “permission-less, public blockchain.”
Now, the second blog of this series continues the search for another potential suspect that accounts for the confusion. It questions the viability of the cornerstone of “permission-less, public blockchain,” consensus protocols.
Here is a takeaway!
The cornerstone of “permission-less, public blockchain” is its trust building mechanism, called consensus protocols, that is intended to replace any central governing authority. But, it comes with some drawbacks.
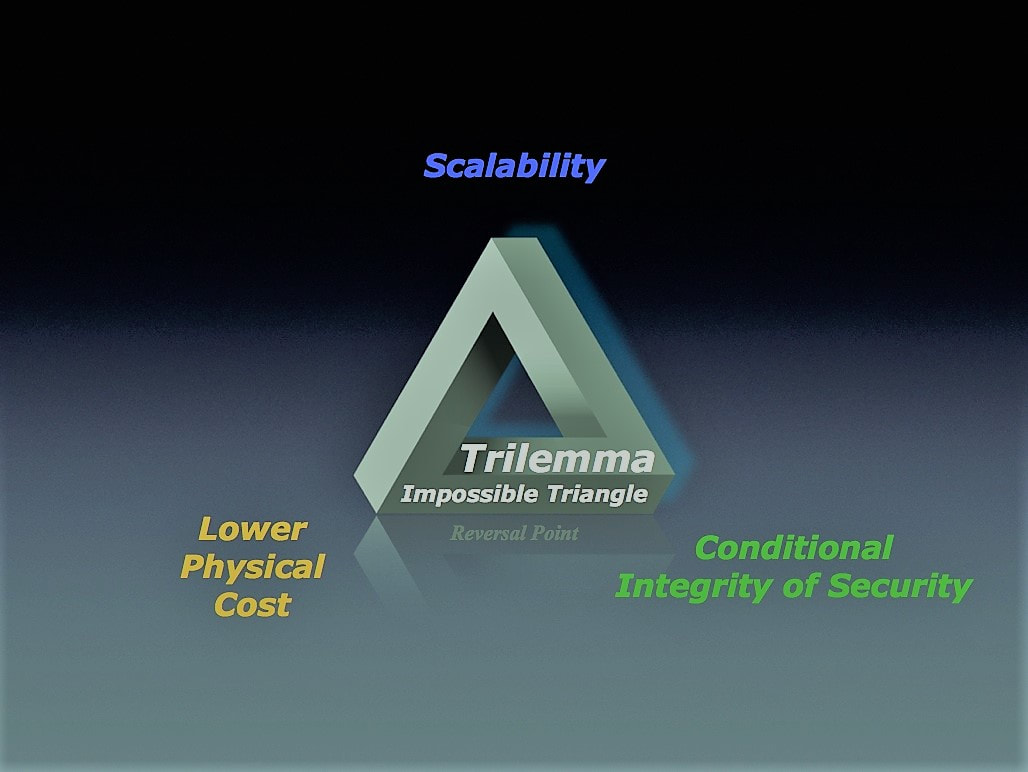
In brief, constraints of current consensus protocols are causing a TRILEMMA situation; in other words, such constraints make it impossible for the system to meet the following three goals at the same time:
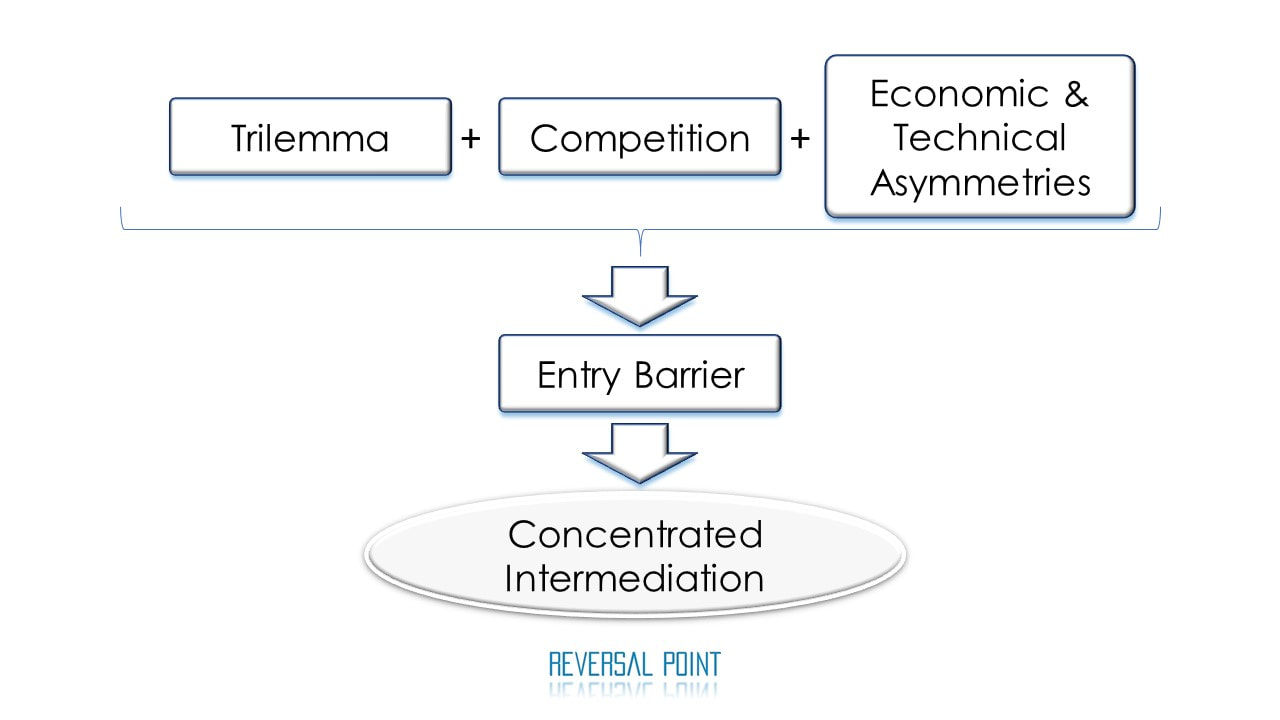
In addition, when competition intensifies, “Trilemma” conspires with the economic and technical asymmetries that are present in the eco-system to build-up entry barriers, which in practice reinforce the fortress of intermediaries. Ultimately, the resulting reality leads to a concentration of intermediaries, thus, disputes the notion of pure peer-to-peer system, or total disintermediation. This paradoxical situation, the gap between reality and the fundamentalistic mantras, could cause confusion.
As a precautionary note, disintermediation is a debatable topic: whether a concentration of intermediaries confronts the spirit of a peer-to-peer notion. Disintermediation notion of a peer-to-peer paradigm is to be challenged later in the series. For now, we question the fundamentalistic notion of “total disintermediation” as a part of peer-to-peer paradigm.
In brief, constraints of current consensus protocols are causing a TRILEMMA situation; in other words, such constraints make it impossible for the system to meet the following three goals at the same time:
- low physical cost (low energy consumption and light hardware computational requirement);
- high scalability (high throughput & fast transaction speed);
- integrity of the system’s security.
In addition, when competition intensifies, “Trilemma” conspires with the economic and technical asymmetries that are present in the eco-system to build-up entry barriers, which in practice reinforce the fortress of intermediaries. Ultimately, the resulting reality leads to a concentration of intermediaries, thus, disputes the notion of pure peer-to-peer system, or total disintermediation. This paradoxical situation, the gap between reality and the fundamentalistic mantras, could cause confusion.
As a precautionary note, disintermediation is a debatable topic: whether a concentration of intermediaries confronts the spirit of a peer-to-peer notion. Disintermediation notion of a peer-to-peer paradigm is to be challenged later in the series. For now, we question the fundamentalistic notion of “total disintermediation” as a part of peer-to-peer paradigm.
Trilemma of Permission-less, Public Blockchain:
1. The cornerstone of “permission-less, public blockchain”
Repeatedly, the cornerstone of permission-less, public blockchain is its trust-building mechanism called consensus protocols. Here is why. Needless to say, the beauty of “permission-less, public blockchain” is that it enables a peer-to-peer system to operate in the absence of any centralised governing party. But here is a catch: because of the absence of a centralised trusted party, its verification and validation process (e.g. mining for “Proof of Work,” minting for “Proof of Stake”) requires an algorithm-based trust-building mechanism, which is operated by consensus protocols in order to build up trust among an unknown number of anonymous stakeholders in an open, unstructured ecosystem. Overall, the technical viability of its consensus algorithm/protocol is essential in executing “permission-less, public blockchain.”
On the other hand, two other types of blockchains—permissioned, private blockchain, and permissioned, federated/consortium blockchains—delegate pre-approved governing stakeholders to control the validation of transactions and security of the system to a great extent.
In a way, they rely on trust-base human governance. And consensus building within such a system would not demand much computational burden. As a result, these systems would face less technical difficulties than “permission-less, public blockchain.” Therefore, these two types of blockchains are characterised as energy efficient, highly scalable (high throughput, fast processing system), and more secure. In summary, these frameworks are more technically feasible, thus, viable for an immediate use when compared with “permission-less, public blockchain” as of today.
Overall, the evolution of consensus protocol is still at an infant stage. And some of the major technical difficulties exist as a hindrance in applications of “permission-less, public blockchain.”
On the other hand, two other types of blockchains—permissioned, private blockchain, and permissioned, federated/consortium blockchains—delegate pre-approved governing stakeholders to control the validation of transactions and security of the system to a great extent.
In a way, they rely on trust-base human governance. And consensus building within such a system would not demand much computational burden. As a result, these systems would face less technical difficulties than “permission-less, public blockchain.” Therefore, these two types of blockchains are characterised as energy efficient, highly scalable (high throughput, fast processing system), and more secure. In summary, these frameworks are more technically feasible, thus, viable for an immediate use when compared with “permission-less, public blockchain” as of today.
Overall, the evolution of consensus protocol is still at an infant stage. And some of the major technical difficulties exist as a hindrance in applications of “permission-less, public blockchain.”
Two Earlier Consensus Protocols:
"Proof of Work" and "Proof of Stake"
Now, let’s narrow our focus on two earlier generations of consensus protocols, Proof of Work (PoW) and Proof of Stake (PoS).
Proof of Work (PoW), is famous for the use case of Bitcoin and arguably[i] the first generation of consensus protocol for “permission-less, public blockchain.” Overall, Bitcoin’s PoW revealed its own limitations and raised issues that need to be resolved in the future. Then, alternative protocols that followed after PoW, including PoS, have been created, more or less, in attempts to resolve some of those issues that PoW raised. That said, no existing protocols has managed to deliver a secure and scalable application yet.
In this historical context, to focus on issues surrounding these first two generations of consensus protocol helps us to paint a big perspective about the issues surrounding “permission-less, public blockchain.”
Here is a good reference for a comparison between these two consensus protocols, PoW and PoS: “Proof of Stake versus Proof of Work”: http://bitfury.com/content/5-white-papers-research/pos-vs-pow-1.0.2.pdf
Proof of Work (PoW), is famous for the use case of Bitcoin and arguably[i] the first generation of consensus protocol for “permission-less, public blockchain.” Overall, Bitcoin’s PoW revealed its own limitations and raised issues that need to be resolved in the future. Then, alternative protocols that followed after PoW, including PoS, have been created, more or less, in attempts to resolve some of those issues that PoW raised. That said, no existing protocols has managed to deliver a secure and scalable application yet.
In this historical context, to focus on issues surrounding these first two generations of consensus protocol helps us to paint a big perspective about the issues surrounding “permission-less, public blockchain.”
Here is a good reference for a comparison between these two consensus protocols, PoW and PoS: “Proof of Stake versus Proof of Work”: http://bitfury.com/content/5-white-papers-research/pos-vs-pow-1.0.2.pdf
2. Economic and Technical Burden of Consensus Protocols:
PoW cases
The Genesis
Now, in order to illustrate what Proof of Work is about, let’s go back to the genesis of Bitcoin, Satoshi Nakamoto’s paper: “Bitcoin: A Peer-to-Peer Electronic Cash System.” (N.D.) Here is the abstract of the paper:
Abstract.
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone. (Nakamoto, N.D., p. 1)
The abstract is compact in compiling essential ideas of PoW.
A node here represents a computer’s CPU connected to the given blockchain network. There are two types of nodes: full node and lightweight node. Full nodes enforce the rules of the given protocol and comply a certain set of requirements. (An overview of node and “full node” is given in the appendix.)
PoW decision making framework employs (1) one-CPU one voting and (2) the longest chain representation. According to the white paper above, Nakamoto’s PoW contemplates the following CONDITIONAL integrity of the system:
1) Conditional Security 1 (No Third Party Condition):
A node here represents a computer’s CPU connected to the given blockchain network. There are two types of nodes: full node and lightweight node. Full nodes enforce the rules of the given protocol and comply a certain set of requirements. (An overview of node and “full node” is given in the appendix.)
PoW decision making framework employs (1) one-CPU one voting and (2) the longest chain representation. According to the white paper above, Nakamoto’s PoW contemplates the following CONDITIONAL integrity of the system:
1) Conditional Security 1 (No Third Party Condition):
| Nakamoto contemplates a peer-to-peer system without any trusted third party. The integrity of peer-to-peer system is CONDITIONAL on the perfect absence of any third party in the validation process. Nakamoto stresses: “[T]he main benefits [of digital signatures] are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network.” (Nakamoto, N.D., p. 1) In other words, any involvement of third party in the validation process could impair the integrity of security of the system. This is to say good-bye to a trust-based human governance model, and hello to a cryptographic proof-based algorithmic governance. This leads to a popular blockchain adjective “trust-less.” |
2) Conditional Immutability (No Redoing Condition):
| Nakamoto contemplates a CONDITIONAL immutability of the historical transaction records. In the abstract, this is expressed indirectly as follows:
In other words, if redoing of the proof of work does not take place, the historical transaction records cannot be changed. This condition is tautologically true. |
Here are two supplemantary notes:
a) One source of risk for the immutability is an attack.
a) One source of risk for the immutability is an attack.
| The length of a chain is commensurate with the CPU power spent to build up the past records. The longer the chain (after a particular block subject to attack), the more expensive it is to change the past records after that block; therefore, the more unlikely to be attacked.
This is a weak assumption for no attack: it does not guarantee the security of the system from attacks by itself. Then, the next condition needs to accompany. |
b) Another source of risk for the immutability is “fork.”
| Fork is a phenomenon in which more than one miner managed to create blocks, all of which refer to the same single previous block, at the same time. This creates multiple branches out of the chain. Because blockchain only recognises one single historical truth about historical transactions, the multi-branch consequence confronts the spirit. As new blocks are added to those multiple branches, here comes the second PoW decision making rule aforementioned: (2) the longest chain representation. Basically, a voting is based on computational power expended. Following this rule, ultimately the longest branch will prevail. In the conclusion section of the white paper, Nakamoto goes: “They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them.” (Nakamoto, N.D., p. 8) |
3) Conditional Security 2 (Trustable Majority CPU-power Condition):
| Nakamoto’s PoW contemplates a guarantee of the system’s security CONDITIONAL on that the majority of CPU-power has no will to cooperate with a malicious party to attack the system:
Simply put, PoW trades off the cost of physically scarce resources, CPU-power and energy, against the CONDITIONAL INTEGRITY of its security. |
- Trade-off 1: There is a trade-off between Physical Cost and Conditional Integrity.
Overall, what Nakamoto contemplates in the abstract of Bitcoin white paper is a CONDITIONAL INTEGRITY of the system’s security, but never suggests any absolute integrity.
In the rest of the chapter, in contemplating peer-to-peer systems, all these terms—“integrity of the system’s security,” security, and integrity—convey these particular CONDITIONAL notions stated above, unless mentioned otherwise.
In the rest of the chapter, in contemplating peer-to-peer systems, all these terms—“integrity of the system’s security,” security, and integrity—convey these particular CONDITIONAL notions stated above, unless mentioned otherwise.
Verification and Validation Process
How are new transactions processed and accepted in the network? It can be roughly sketched as below without going into details.
- Broadcast of a New Transaction: A new transaction is broadcast to all nodes.
- Transaction-level Verification: Each full node independently verifies every new incoming transaction.
- Making a Pending Block: Mining nodes collect new transactions into a pending block.
- Block-level Validation: Mining nodes, expending physically scarce resources, work on solving cryptographic puzzle (finding a difficult proof-of-work) for its block.
- Broadcast of a New Block: When a mining node solves the puzzle (finds a proof-of-work,) it broadcasts the new block to all nodes.
- Peer-review: Full nodes do peer-review the validity of the new block and accept it only if all transactions in it are valid and not already spent.
- Consensus: A full node can express its own consensus on the new block by creating a next block to the newly accepted block in the chain.
In the last two stages, 6-7, only the first accepted block counts. Any other blocks that went into the peer-review stage from other mining nodes are rejected and irrelevant.
Here is why. For a new cycle of transactions to start, a new payee needs to be convinced that the past owner did not double spend the value the payee received. In other words, in order not to give the previous owner any chance to double spend the value, it is imperative to accept the very first block approved in the process. Nakamoto describes this requirement as follows:
We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint [a trusted central monetary authority in the metallic standard era] based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced …, and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received. (Nakamoto, N.D., p. 2)
Now, let’s sum up what we have learnt.
Proof of Work is a trust-building consensus protocol that regulates the verification and validation of transactions. It requires:
Only the first miner who solves the cryptographic puzzle will earn the mining reward and the rest of miners will have no economic gain after expending their computational powers.
In a way, the probability that a miner manages to earn the mining reward depends on the physical cost: the expended amount of physically scarce resource (CPU-power and energy consumption.) Thus, that probability is commensurate with its computational power relative to the total computational power in the eco-system. In other words, in PoW, a miner with a share of computational power p has the same probability p to earn the mining reward.
This incentive mechanism intensifies competition among miners to solve the problem faster than any other peers. Therefore, it increases the demand for physically scarce resources: a higher computational power and energy consumption.
Proof of Work is a trust-building consensus protocol that regulates the verification and validation of transactions. It requires:
- validators (miners) to use physically scarce resources (a high computational power and energy) to solve cryptographic puzzles to complete the validation process: generate and validate a new block out of multiple previously peer reviewed transactions that are compliant with the given protocol.
- every full node to do peer-review the validity of all transactions and all blocks created by miners.
Only the first miner who solves the cryptographic puzzle will earn the mining reward and the rest of miners will have no economic gain after expending their computational powers.
In a way, the probability that a miner manages to earn the mining reward depends on the physical cost: the expended amount of physically scarce resource (CPU-power and energy consumption.) Thus, that probability is commensurate with its computational power relative to the total computational power in the eco-system. In other words, in PoW, a miner with a share of computational power p has the same probability p to earn the mining reward.
This incentive mechanism intensifies competition among miners to solve the problem faster than any other peers. Therefore, it increases the demand for physically scarce resources: a higher computational power and energy consumption.
Physical Cost
The physical cost is one of many issues of Bitcoin’s PoW. Now let’s have an overview of physical cost: energy consumption and hardware computation requirements.
Energy Intensity
Because of the absence of a centralised trusted party, the PoW verification and validation (mining) process requires massive energy to establish trust in the system. Alex de Vries, a.k.a. Digiconomist has been raising the issue of unsustainable energy consumption of Bitcoin and tracking “Bitcoin Energy Consumption Index” to put the issue in perspective. (De Vries, 2018)
Source: https://digiconomist.net/bitcoin-energy-consumption
As of the 2nd of February, 2018 (De Vries, 2018):
1) The annual ESTIMATED energy consumption of BitCoin is 46.86 TWh (TERA WATT HOUR).
Now, BitCoin is traded among a limited number of investors. Based on these estimates as of today, we can have a big picture. If it were to become a currency regime (a public utility), BitCoin could breakdown our energy system today. It would not be sustainable. (De Vries, 2018)
This Bitcoin case illustrates that for a digital currency to serve as a viable monetary regime, a public utility, it would be a necessary condition, if not a sufficient one, that it guarantees a sustainable energy efficiency. Bitcoin does not meet this necessary condition.
These estimates are changing as time goes by. Going forward, we need to monitor Digiconomist’s “Bitcoin Energy Consumption Index”.
Source: https://digiconomist.net/bitcoin-energy-consumption
As of the 2nd of February, 2018 (De Vries, 2018):
1) The annual ESTIMATED energy consumption of BitCoin is 46.86 TWh (TERA WATT HOUR).
- It is comparable to the annual energy consumption of Iraq.
- It can power 4,339,330 US households.
- vs. 0.01 Wh per transaction for VISA energy consumption.
- In other words, one single transaction of BitCoin can power 18.3 US households for one day.
Now, BitCoin is traded among a limited number of investors. Based on these estimates as of today, we can have a big picture. If it were to become a currency regime (a public utility), BitCoin could breakdown our energy system today. It would not be sustainable. (De Vries, 2018)
This Bitcoin case illustrates that for a digital currency to serve as a viable monetary regime, a public utility, it would be a necessary condition, if not a sufficient one, that it guarantees a sustainable energy efficiency. Bitcoin does not meet this necessary condition.
These estimates are changing as time goes by. Going forward, we need to monitor Digiconomist’s “Bitcoin Energy Consumption Index”.
Ever-increasing Hardware Computational requirement:
As a blockchain system expands in scale, validation becomes more difficult. And an increasing difficulty would require more physically scarce resources: more expensive hardware with a better computational power and more energy consumption. The difficulty at the end of 2017 is multiplied by ONE BILLION folds since 2010, according to the historical chart of the difficulty of Bitcoin in the following link. (www.blockchain.com, N.D.)
https://blockchain.info/charts/difficulty?scale=1×pan=all
https://blockchain.info/charts/difficulty?scale=1×pan=all
Trade-off 2: Trade-off between scalability and physical cost:
Overall, the history of Bitcoin’s PoW revealed that there is a trade-off tendency between scalability (throughput and transaction speed) and physical cost (energy consumption and hardware computational requirement). Simply put, in order to reduce physical cost, it needs to sacrifice scalability. In order to enhance scalability, it has to meet more physical cost.
- Trade-off 2: There is a trade-off between physical cost and scalability.
That said, reality is little more complex, since energy efficiency can improve even if difficulty (hardware computational requirements) increase as the demand for scalability (more throughput and faster transaction speed) intensifies. (especially when energy efficiency of hardware drastically improves, the consequential energy consumption could decline while the computational requirements increase.) This could alter the total net impact on physical cost, while the scalability demand increases. For now, we assume energy efficiency of hardware to be constant for the sake of argument.
Trilemma
So far, we have two trade-off relationships.
Moreover, physical cost acts as a channel between scalability and integrity of security to produce another trade-off. Cut it short, we have a trilemma: we cannot satisfy all these three goals at the same time:
This trilemma sets the constraints of PoW.
- Trade-off 1: There is a trade-off between Physical Cost and Conditional Integrity.
- Trade-off 2: There is a trade-off between physical cost and scalability.
Moreover, physical cost acts as a channel between scalability and integrity of security to produce another trade-off. Cut it short, we have a trilemma: we cannot satisfy all these three goals at the same time:
- High Scalability;
- Low Physical Cost;
- Sound “Conditional Integrity of Security”;
This trilemma sets the constraints of PoW.
With the trilemma constraint, another factor comes in to drive an increase in physical cost: namely, competition. In order to earn mining reward, miners compete against each other to complete the validation process faster than their competitors. This incentivises them to increase scalability; then, while maintaining the level of security, the trilemma forces miners to increase physical cost: upgrade their hardware computational power and increase energy consumption. Simply put, with other conditions constant, the higher the competition, the higher physical cost—more energy consumption and a higher hardware computing power requirement.
Moreover, in the eco-system there are asymmetries existing among stakeholders in the individual’s ability to upgrade ones own hardware computational power and increase energy consumption. These are economic and technical asymmetries.
Then, competition together with economic and technical asymmetries could build up a higher entry barrier, simply because it requires more economic and technical resources for them to participate in validation as the competition intensifies.
Moreover, in the eco-system there are asymmetries existing among stakeholders in the individual’s ability to upgrade ones own hardware computational power and increase energy consumption. These are economic and technical asymmetries.
Then, competition together with economic and technical asymmetries could build up a higher entry barrier, simply because it requires more economic and technical resources for them to participate in validation as the competition intensifies.
Digiconomist (2014) summarises all these chain reactions in a compact statement.
PoW mining is not just an energy-wasting process, it is also an extremely competitive process by nature. Participants are constantly tempted to improve their mining efficiency, which forces other to join in an arms race or drop out. It leads to a situation where profit maximization is not just desirable, but also a necessity. As increasing scale means more costs benefits, hashrate will cluster together. (Digiconomist, 2014)
Recalling the historical fact: the difficulty at the end of 2017 is multiplied by ONE BILLION folds since 2010. (www.blockchain.com, N.D.) ONE BILLION-fold difficulty during 7 years together with the increase in energy intensity must have built up a sky-high entry barrier in the Bitcoin mining space. A high entry barrier can cause a highly concentrated system, either oligopoly or monopoly. This accords with the following inauspicious fact:
70% of Bitcoin mining (measured in hashrate) is dominated by only top FIVE miners.
(BTC.com, ND; Kasireddy, 2017)
The concentration of miners is an ironical consequence, recalling Nakamoto’s two security conditions:
- Nakamoto’s conditional security 1: (No Third Party Condition): “[T]he main benefits [of digital signatures] are lost if a trusted third party is still required to prevent double-spending.” (Nakamoto, N.D., p. 1)
- Nakamoto’s conditional security 2: (Trustable Majority CPU-power Condition): “As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers.” (Nakamoto, N.D., p. 1)
Nonetheless, it’s important to remember that each node is running on a computer system owned and controlled by a particular person or organization, so the blockchain cannot force it to do anything. The purpose of the chain is to help honest nodes to stay in sync, but if enough of its participants choose to change the rules, no earthly power can stop them. (Greenspan, 2017)
It would be legitimate for us to question whether the concentration consequence blows up Nakamoto’s conditional security. It seems as if Nakamoto did not contemplate friction—economic and technical asymmetries that could lead to a concentration of the third party—when he conceived the no-friction peer-to-peer paradigm. (Some would argue that miners are not a third party. I take a different position that they could be a potential third party, depending on the social, economic and political context given.)
Overall, Bitcoin is a great experiment in the sense that it has revealed its limitations and raised pending issues to be resolved for the development of future generations. In this sense, it would be too naïve to admire Bitcoin as a solution ready to serve as a new currency regime.
Overall, Bitcoin is a great experiment in the sense that it has revealed its limitations and raised pending issues to be resolved for the development of future generations. In this sense, it would be too naïve to admire Bitcoin as a solution ready to serve as a new currency regime.
Trade-off in the Transition from PoW to PoS:
In order to alleviate the physical cost imposed on PoW, a new consensus protocol was innovated: Proof of Stake (PoS). PoS was first adopted by Peercoin. Later, it was popularised by Ethereum. That said, the transition from PoW to PoS has proven another case of trade-off between the physical cost and the conditional integrity of the system. Here are two takeaways about the consequences of the trade-off arising from this transition:
- Compromised Security:
- Concentration Curse:
Compromised Security 1: Architecture of PoS
In order to improve energy efficiency, PoS has drastically simplified the consensus building mechanism. While the validation process is called mining for PoW, for PoS the process is called minting. Here is a comparison between PoW’s mining and PoS’s minting.
In a way, the PoS’s architecture removed the expenditure requirement of physically scarce resources, when compared with Bitcoin’s PoW. It might have potentially suffered from the constraints of the trilemma: in order to achieve less physical cost, while maintaining its ambition for scalability, it might have sacrificed integrity of the system’s security. From this perspective, it would be legitimate if some raise concern that pure PoS applications have potentially compromised the integrity of the system’s security, by not demanding physically scarce resources in the validation process.
- PoW requires the mining process to expend physically scarce resources, such as computing power and energy.
- PoS does not demand the minting process to expend much of physically scarce resources. PoS gives a node a chance to generate a valid block commensurate with the proportion of the node’s stake to the eco-system’s total stake: the chance equals to the ratio of a user’s balance of funds to the total amount of currency in circulation.
In a way, the PoS’s architecture removed the expenditure requirement of physically scarce resources, when compared with Bitcoin’s PoW. It might have potentially suffered from the constraints of the trilemma: in order to achieve less physical cost, while maintaining its ambition for scalability, it might have sacrificed integrity of the system’s security. From this perspective, it would be legitimate if some raise concern that pure PoS applications have potentially compromised the integrity of the system’s security, by not demanding physically scarce resources in the validation process.
“pure proof of stake approaches pose substantial security threats that cannot be recreated in proof of work systems (including Bitcoin). These problems are inherent to proof of stake algorithms, as proof of stake consensus is not anchored in the physical world (cf. with hashing equipment in proof of work).
That is why virtually all of currencies relying on proof of stake use additional mechanisms to address security issues. (…)
Still, these improvements can be seen as ad-hoc and incomplete”
(BitFury Group, 2015)
In a way, the transition from PoW to PoS has likely traded the integrity of the validation process for a better energy efficiency.
A BitFury’s white paper, “Proof of Stake versus Proof of Work,” lists up potential security issues that a pure PoS system could suffer from. Here are the two examples (BitFury Group, 2015):
1) Nothing at Stake Problem:
A BitFury’s white paper, “Proof of Stake versus Proof of Work,” lists up potential security issues that a pure PoS system could suffer from. Here are the two examples (BitFury Group, 2015):
1) Nothing at Stake Problem:
| PoS does not demand validators to expend much of physically scarce resources. In a case of “fork,” a node can simultaneously mint different branches out of the single chain, without risking any stake. This “nothing at stake problem” allows multiple branches to grow out of the original single chain and could compromise the notion of one single truth of transaction history. |
2) Long Range Attack;
| Since PoS does not impose much of physically scarce resource on its validation process. An attacker can easily re-do the PoS going back to the very beginning of the chain. Put it into a perspective, this is a violation of Conditional Immutability (No Redoing Condition) for the case of Proof of Work. Even in the PoS context, redoing compromises integrity of the system’s security. |
A more details of these issues can be found in the paper: http://bitfury.com/content/5-white-papers-research/pos-vs-pow-1.0.2.pdf.
Compromised Security 2: Attack-prone Smart Contract
Smart contract is another special feature of Ethereum’s PoS, besides its reduction in physical cost. That said, it is not simple to find THE definition of “smart contract.” “The term “smart contract” has no clear and settled definition. (Stark, 2016) Gideon Greenspan puts his view about “smart contract” into a perspective:
“when smart people hear the term “smart contracts”, their imaginations tend to run wild. They conjure up dreams of autonomous intelligent software, going off into the world, taking its data along for the ride.
Unfortunately the reality of smart contracts is far more mundane than all that:
A smart contract is a piece of code which is stored on an blockchain, triggered by blockchain transactions, and which reads and writes data in that blockchain’s database.
That’s it. Really”.
(Greenspan, 2016)
Then, Wikipedia goes:
A smart contract is a computer protocol intended to digitally facilitate, verify, or enforce the negotiation or performance of a contract. (Wikipedia, N.D.)
Smart contracts of Ethereum applications have been attacked a few times in the past and revealed the poor integrity of its security. As to be discussed later in this series, the security of smart contract is guaranteed as long as its applications operate within the architecture of Ethereum, in which smart contracts are embedded. In a way, when smart contracts need to work with external systems, their integrity can be significantly compromised. Designing safe interfaces to guarantee secure interactions between a smart contract and external systems is a challenging work. Overall, a smart contract is bound to be prone to attacks. Thus, its security can be easily compromised. (Greenspan, 2016)
Concentration Curse 1: Architecture of PoS
Since in validation PoS would give more weight to a node with a more stake-holding, the architecture of PoS, by design, promotes concentration. The design of the architecture itself would compromise the notion of a democratic system that those blockchain idealists contemplated. Would it be surprising, if the founders intentionally designed the consensus protocol in order to privilege their stake power in the name of energy efficiency?
Here is a relevant statement made by the Ethereum founder, Vitalik Buterine.
Here is a relevant statement made by the Ethereum founder, Vitalik Buterine.
all “pure” proof-of-stake systems are ultimately permanent nobilities where the members of the genesis block allocation always have the ultimate say. No matter what happens ten million blocks down the road, the genesis block members can always come together and launch an alternate fork with an alternate transaction history and have that fork take over. (Buterin, 2014)
Basically, the founder openly admitted that the founding members (the genesis block members) can intervene any time at their will the given order of the system in order to alter the history of the past transactions. The founder calls it “nobilities.” But, it could sound a dictatorship to some, thus, compromises the peer-to-peer notion of Ethereum. At least, this statement serves the founder’s declaration that PoS has weak self-sufficiency in the integrity of its security.
In a way, arguably, PoS has failed to say good-bye to a trust-based human governance model as long as it needs to rely on the genesis block that represents the founder’s stake; it would not serve as a self-sufficient cryptographic proof-based governance model. So, a more essential question is whether it should be categorised as a full-fledged “permission-less, public blockchain” system.
In a way, arguably, PoS has failed to say good-bye to a trust-based human governance model as long as it needs to rely on the genesis block that represents the founder’s stake; it would not serve as a self-sufficient cryptographic proof-based governance model. So, a more essential question is whether it should be categorised as a full-fledged “permission-less, public blockchain” system.
Concentration Curse 2: PoS’s Fast Growth Rate
In addition, here is another paradoxical takeaway. On one hand, the transition was made for a better efficiency for physically scarce resources. On the other, there is a counter-productive fact: the growth rate of the demand for hardware computational power might progressively increase for PoS. Analogous to Bitcoin’s PoW’s case, as the size of blockchain grows, it requires more computational power, as a result, forces out ordinary users of the eco-system. The increase in demand for hardware’s computational power reinforces concentration that is also driven by the design of Ethereum’s PoS.
Ethereum, growing faster than Bitcoin, could face bigger concentration issues than PoW. (Maas, 2017)
Overall Assessment of the Transition from PoW to PoS:
The issues surrounding the transition from PoW to PoS presented above, revealed a trade-off between physical cost (the economic and technical cost) and conditional integrity of security. It proves to be difficult to satisfy these two goals at the same time:
This dilemma is a part of the trilemma discussed earlier. In this sense, the transition ends up suffering from the trilemma.
In addition, the very design of PoS’s architecture and the growth rate of the use of its applications accounted for PoS’ concentration curse, the contrary notion to disintermediation.
As of today, this trilemma strains and compromises the viability of “permission-less, public blockchain.”
We would need a revolutionary game-theory-base consensus protocol to resolve the trilemma—in other words, to meet all these three requirements at the same time.
Overall, the concentration tendency would promise the territory for intermediaries and would compromise the notion of disintermediation and pure peer-to-peer system.
- Lower Physical Cost (energy consumption, hardware computational power);
- Conditional Integrity of the System’s Security
This dilemma is a part of the trilemma discussed earlier. In this sense, the transition ends up suffering from the trilemma.
In addition, the very design of PoS’s architecture and the growth rate of the use of its applications accounted for PoS’ concentration curse, the contrary notion to disintermediation.
As of today, this trilemma strains and compromises the viability of “permission-less, public blockchain.”
We would need a revolutionary game-theory-base consensus protocol to resolve the trilemma—in other words, to meet all these three requirements at the same time.
Overall, the concentration tendency would promise the territory for intermediaries and would compromise the notion of disintermediation and pure peer-to-peer system.
Implication
Satoshi Nakamoto imposed three conditions in contemplating his peer-to-peer paradigm.
The cornerstone of “permission-less, public blockchain” is its consensus protocols. As of today, at an infant stage in its evolution, consensus protocol faces a trilemma as well as other technical limitations.
As a result, it ends up shaping non-scalable, pseudo oligopolistic ecosystems, empowering new emerging intermediaries through “Concentration Curse.” This situation violates one of premises of Satoshi Nakamoto’s conditional security for a peer-to-peer system, no third party condition. This creates a paradoxical reality to those fundamentalistic notions.
As another result, the transition from PoW to PoS sacrificed its conditional integrity of the system’s security, by eliminating the validation criteria of demanding physically scarce resources. The transition has traded the integrity of PoS’s security for a better economic and technical efficiency.
In this setting, the trilemma of “permission-less, public blockchain” have empowered intermediaries, both incumbents and new breeds, not only in its own space, but also in the rest of blockchain universe—"permissioned, private blockchain” and “permissioned, federated/consortium blockchains,”—by not delivering what it promised.
In this picture, incumbent intermediaries can be benefactors of blockchain depending on the context. Of course, this does not automatically guarantee the job security of their employees. They are bound to be victims of streamlining (layoff) due to new efficiencies created by these permissioned blockchains.
When it comes to macroeconomic consequences, simply put, innovation kills jobs in one place and creates jobs in another. The net effect is not that simple. If its net effect in the overall job creation is negative, productivity gain from the innovation could be negative for growth; further, the innovation could be deflationary. But, it would depend on all other factors.
Given the paradoxical reality, what would those blockchain-idealists try to achieve with Blockchain? Are they ambitious rent-seekers veiled in libertarian mantras? Or are they hypnotising themselves (as well as us) with their own deceptive mantras?
A hope might remain in the future development of consensus protocols. Some day in the future, a revolutionary game-theory based consensus protocol that the world has never seen, might be innovated and resolve these issues. It is an open question.
As a precautionary note regarding disintermediation, later in the series, a contrary alternative view is presented that the original goal of blockchain aims at “distributed intermediation,” not “total disintermediation.” This alternative view reflects the reality of blockchain as of today, but confronts Satoshi Nakamoto’s conditional security 1, no third party condition. This questions whether Nakamoto missed something in crafting his plan; or it was a hidden ingredient for his deceptive plan against our expectation (an expectation that he is a liberator of our transaction culture).
The next blog of this series further focuses on “Concentration Curse” of “permission-less, public blockchain.” It casts a notion of paradox.
Michio Suginoo
- Conditional Security 1 (No Third Party Condition): the perfect absence of any third party in the validation process. (disintermediation)
- Conditional Immutability (No Redoing Condition): no redoing of the validation process
- Conditional Security 2 (Trustable Majority CPU-power Condition): the majority of CPU-power has no will to cooperate with a malicious party to attack the system.
The cornerstone of “permission-less, public blockchain” is its consensus protocols. As of today, at an infant stage in its evolution, consensus protocol faces a trilemma as well as other technical limitations.
As a result, it ends up shaping non-scalable, pseudo oligopolistic ecosystems, empowering new emerging intermediaries through “Concentration Curse.” This situation violates one of premises of Satoshi Nakamoto’s conditional security for a peer-to-peer system, no third party condition. This creates a paradoxical reality to those fundamentalistic notions.
As another result, the transition from PoW to PoS sacrificed its conditional integrity of the system’s security, by eliminating the validation criteria of demanding physically scarce resources. The transition has traded the integrity of PoS’s security for a better economic and technical efficiency.
In this setting, the trilemma of “permission-less, public blockchain” have empowered intermediaries, both incumbents and new breeds, not only in its own space, but also in the rest of blockchain universe—"permissioned, private blockchain” and “permissioned, federated/consortium blockchains,”—by not delivering what it promised.
In this picture, incumbent intermediaries can be benefactors of blockchain depending on the context. Of course, this does not automatically guarantee the job security of their employees. They are bound to be victims of streamlining (layoff) due to new efficiencies created by these permissioned blockchains.
When it comes to macroeconomic consequences, simply put, innovation kills jobs in one place and creates jobs in another. The net effect is not that simple. If its net effect in the overall job creation is negative, productivity gain from the innovation could be negative for growth; further, the innovation could be deflationary. But, it would depend on all other factors.
Given the paradoxical reality, what would those blockchain-idealists try to achieve with Blockchain? Are they ambitious rent-seekers veiled in libertarian mantras? Or are they hypnotising themselves (as well as us) with their own deceptive mantras?
A hope might remain in the future development of consensus protocols. Some day in the future, a revolutionary game-theory based consensus protocol that the world has never seen, might be innovated and resolve these issues. It is an open question.
As a precautionary note regarding disintermediation, later in the series, a contrary alternative view is presented that the original goal of blockchain aims at “distributed intermediation,” not “total disintermediation.” This alternative view reflects the reality of blockchain as of today, but confronts Satoshi Nakamoto’s conditional security 1, no third party condition. This questions whether Nakamoto missed something in crafting his plan; or it was a hidden ingredient for his deceptive plan against our expectation (an expectation that he is a liberator of our transaction culture).
The next blog of this series further focuses on “Concentration Curse” of “permission-less, public blockchain.” It casts a notion of paradox.
Michio Suginoo
Note
[i] In his attempt to introduce “proof of work,” Satoshi Nakamoto himself referred to Hashcash in his white paper, “Bitcoin: A Peer-to-Peer Electronic Cash System.”
Appendix
Nodes:
Source:
Here is a brief about Nodes from the sources above:
A node represents a computer that connects to the Bitcoin network. There are two types of nodes: full nodes and lightweight nodes.
A full node downloads every block and transaction and check whether they comply with Bitcoin's core consensus rules. Full nodes simply reject any transaction or block that violates the consensus rules even if other nodes on the network thinks that it is valid.
“Running a full node is the only way you can use Bitcoin in a trustless way.”
Lightweight nodes skip the process, which full nodes do without fail (the process to download every block and transaction and check (verify or validate?) whether they comply with Bitcoin's core consensus rules). They rather follow “whatever the majority of mining power says.” Therefore, they are bound to be naïve and vulnerable to attack.
"Lightweight nodes do whatever the majority of mining power says. Therefore, if most of the miners got together to increase their block reward, for example, lightweight nodes would blindly go along with it."
Furthermore, to preserve the integrity of the entire eco-system, it is important that the majority of nodes are full nodes.
"Most nodes on the network are lightweight nodes instead of full nodes, but full nodes form the backbone of the network. (…)
In practice, miners are unlikely to attempt anything like the above scenario as long as full nodes are prevalent because the miners would lose a lot of money. But the incentives completely change if everyone uses lightweight nodes. In that case, miners definitely do have an incentive to change Bitcoin's rules in their favor. It is only reasonably secure to use a lightweight node because most of the Bitcoin economy uses full nodes.
Therefore, it is critical for Bitcoin's survival that the great majority of the Bitcoin economy be backed by full nodes, not lightweight nodes."
- BitcoinWiki: https://en.bitcoin.it/wiki/Full_node;
- “Full node: What is the difference between running a node and mining?”: https://www.reddit.com/r/BitcoinBeginners/comments/2rpmyl/what_is_the_difference_between_running_a_node_and/
Here is a brief about Nodes from the sources above:
A node represents a computer that connects to the Bitcoin network. There are two types of nodes: full nodes and lightweight nodes.
A full node downloads every block and transaction and check whether they comply with Bitcoin's core consensus rules. Full nodes simply reject any transaction or block that violates the consensus rules even if other nodes on the network thinks that it is valid.
“Running a full node is the only way you can use Bitcoin in a trustless way.”
- "At minimum, a full node must download every transaction that has ever taken place, all new transactions, and all block headers."
- "Additionally, full nodes must store information about every unspent transaction output until it is spent. By default full nodes are inefficient in that they download each new transaction at least twice, and they store the entire block chain (>60 GB) forever, even though only the unspent transaction outputs (<2 GB) are required."
Lightweight nodes skip the process, which full nodes do without fail (the process to download every block and transaction and check (verify or validate?) whether they comply with Bitcoin's core consensus rules). They rather follow “whatever the majority of mining power says.” Therefore, they are bound to be naïve and vulnerable to attack.
"Lightweight nodes do whatever the majority of mining power says. Therefore, if most of the miners got together to increase their block reward, for example, lightweight nodes would blindly go along with it."
Furthermore, to preserve the integrity of the entire eco-system, it is important that the majority of nodes are full nodes.
"Most nodes on the network are lightweight nodes instead of full nodes, but full nodes form the backbone of the network. (…)
In practice, miners are unlikely to attempt anything like the above scenario as long as full nodes are prevalent because the miners would lose a lot of money. But the incentives completely change if everyone uses lightweight nodes. In that case, miners definitely do have an incentive to change Bitcoin's rules in their favor. It is only reasonably secure to use a lightweight node because most of the Bitcoin economy uses full nodes.
Therefore, it is critical for Bitcoin's survival that the great majority of the Bitcoin economy be backed by full nodes, not lightweight nodes."
References
- BitFury Group. (2015, 9 13). Proof of Stake versus Proof of Work. Retrieved from BitFury.com: http://bitfury.com/content/5-white-papers-research/pos-vs-pow-1.0.2.pdf
- BlockchainHub. (ND). Blockchains & Distributed Ledger Technologies. Retrieved 1 19, 2018, from BlockchainHub: https://blockchainhub.net/blockchains-and-distributed-ledger-technologies-in-general/
- Brosens, T. (2017, 10 13). Why Bitcoin transactions are more expensive than you think. Retrieved from ING: https://think.ing.com/opinions/why-bitcoin-transactions-are-more-expensive-than-you-think/
- BTC.com. (ND). Pool Distribution. Retrieved from BTC.com: https://btc.com/stats/pool
- Buterin, V. (2014, 7 5). On stake. Retrieved from blog.ethereum.org: https://blog.ethereum.org/2014/07/05/stake/
- De Vries, A. (2018, 2 2). Bitcoin Energy Consumption Index. Retrieved from Digiconomist: https://digiconomist.net/bitcoin-energy-consumption
- Digiconomist. (2014, 6 16). A 51% attack: the sum of all fears? Retrieved from Digiconomist.net: https://digiconomist.net/51_attack_sum_of_all_fears/
- Digiconomist. (2014, 7 7). Understanding Economies of Scale. Retrieved from: Digiconomist: https://digiconomist.net/understanding_economies_of_scale/
- Digiconomist. (2016, 2 26). How Limited Block Size May Centralize The Use Of Bitcoin. Retrieved from Digiconomist: https://digiconomist.net/how-limited-block-size-may-centralize-the-use-of-bitcoin
- Esposito, O. (2017, 5 24). The new intermediaries at work behind the blockchain. Retrieved 1 18, 2018, from L'Atelier BNP Paribas: https://atelier.bnpparibas/en/fintech/article/intermediaries-work-blockchain
- Greenspan, G. (2016, 4 12). Beware impossible smart contract. Retrieved from multichain.com: https://www.multichain.com/blog/2016/04/beware-impossible-smart-contract/
- Greenspan, G. (2017, 5 4). Blockchain Immutability Myth. Retrieved from www.multichain.com: https://www.multichain.com/blog/2017/05/blockchain-immutability-myth/
- Greenspan, G. (2017, 5 4). The Blockchain Immutability Myth. Retrieved from www.multichain.com: https://www.multichain.com/blog/2017/05/blockchain-immutability-myth/
- Kasireddy, P. (2017, 12 11). Fundamental challenges with public blockchains. Retrieved from Medium: https://medium.com/@preethikasireddy/fundamental-challenges-with-public-blockchains-253c800e9428
- Maas, T. (2017, 10 5). Criticizing Ethereum — weaknesses of “the internet 3.0”. Retrieved from hackernoon.com: https://hackernoon.com/the-top-critiques-on-ethereum-a-bubble-waiting-to-pop-6ccf9b577d11
- Nakamoto, S. (N.D.). Bitcoin: A Peer-to-Peer Electronic Cash System. NA: www.bitcom.org. Retrieved 1 31, 2018, from http://www.bitcoingroup.com.au/satoshi-whitepaper/
- Stark, J. (2016, 6 4). Making Sense of Blockchain Smart Contracts. Retrieved from Coindesk.com: https://www.coindesk.com/making-sense-smart-contracts/
- Van Noort , W. (2017, 10 23). NRC checkt: ‘Een bitcointransactie voorziet huis maandlang van energie’: Dat meldde RTL Z en ook vakblad De Ingenieur nam die conclusie over. Retrieved from www.nrc.nl: https://www.nrc.nl/nieuws/2017/10/23/nrc-checkt-een-bitcointransactie-voorziet-huis-maandlang-van-energie-13641170-a1578339
- www.blockchain.com. (N.D.). Difficulty. Retrieved from www.blockchain.com: https://blockchain.info/charts/difficulty?scale=1×pan=all